by BehindJava
What are Client Certificates in Microservices
In this tutorial, we are going to learn about Client Certificates in detail.
Client Certificates
- Client certificate is a method for authenticating the API users.
- A Client certificate file (public & private key pair) is used.
- No encryption of data is done by the client certificate.
- When API caller i.e., client makes an API call and connects to the server, then the server validates the client certificate and grants the access.
- This process is called TLS handshake.
Working of Client Certificate
For example, one of the ways of authenticating the API users is basic authentication, where you pass a username and password in the header to the server, and the server validates the username password against a database of usernames and passwords.
- And then if the username and password match, then you can access the resource or make the API call.
- So the client certificate is just another method of authenticating a user that is trying to access a resource or making the API call.
- And there is a client certificate file involved, which is an asymmetric encryption, public key and private key.
- And this key is not used to encrypt any data, so it’s not part of encrypting the data between the server and client.
- There is another certificate that is used for that or for the SSL connection.
- when API call or the client makes an API call or tries to access a resource, a protected resource on the server, the server validates the client certificate.
- If the certificate is valid, then access is granted and this process is called TLS handshake.
We can see it in this picture.
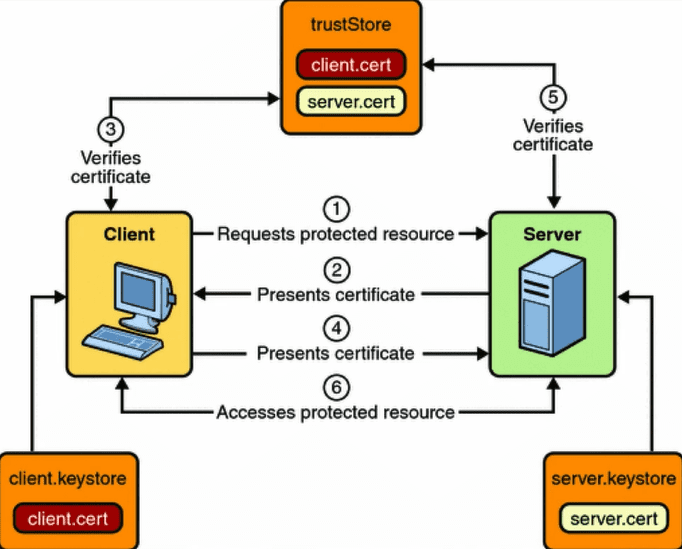
- So the client has a certificate and the server also has a certificate.
- These certificates are issued by a valid certificate authority and are stored in a trusted certificate store.
- So the client tries to access a protected resource on the server. Where it can be an API.
- The server presents its certificate to a client and the client validates it so that it’s got established a secure connection to the server.
- If the certificate is valid, the Client establishes the secure connection and then presents its client certificate to the server over that secure connection.
- The server also validates the client certificate, and if it’s valid, then access is granted to their clients so that the client can access their protected resources.